The Importance of User, Roles and Permissions for System Security
Digital wrongdoing is a projection each association needs to manage. Phishing, extortion, interruption, insider dangers are some brutal realities of the virtual world. The patterns in every one of these zones have significant and complex effect on framework security.
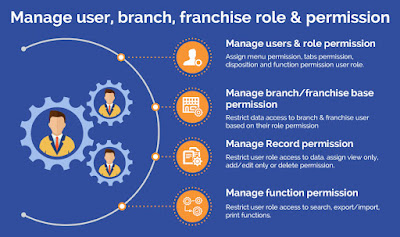
In
membership management software
The best practices for securing your membership software users, roles, and permissions are based on the following ideas:
Review
your roles
Know the
defaults
It is basic to be mindful about falling authorizations made by contributed modules since network contributed modules are not exceptionally anchor. Despite the fact that Role Management in membership software is a troublesome errand, in any case, a few modules concede jobs upon record creation. It is prescribed to keep learning about the defaults since most security warnings for contributed modules manifest because of cross-site scripting (XSS) vulnerabilities. Such situations occur on module organization screens wherein client provided information isn't deliberately sifted. It is prompted that the consents as for the rule of minimum benefit be given to clients with total need.
Assess
your elevated permissions
It is especially imperative to examine certain permission
previously it is made accessible to users with separate roles in light of the
fact that the equivalent can permit full control of your framework. It is
educated to look at the whole rundown regarding permission fastidiously to
guarantee that roles have just the consents that they require for their
capacity. If there should be an occurrence of any defenselessness or danger,
consider expelling consents from a role – it's simpler to include an
authorization later or make another middle of the road role than to re-establish
your database from reinforcements and illuminate users of an anticipated
security rupture.
Guarantee users are offered access to data with least/no
rights to adjust or change without consent.
A role is basically a lot of consents, called abilities,
that you allocate to a gathering of users on your framework. A default role can
be of the accompanying sorts:
- Admin
- Editor
- Author
- Subscriber
- Super Admin
An explicit activity of capacity that a user is allowed to
finish is called Capability. For instance, distributing and altering are two
unique capacities and a user can be given the privileges of altering or
distributing or both in the meantime.
An ability is an explicit activity that a user is allowed to
finish. For instance, altering in framework usefulness is one particular
ability while distributing a usefulness is another capacity. Capacities could
be of various sorts which incorporates include, altering and erasing
usefulness, making classifications, characterizing joins, directing remarks,
overseeing modules and subjects, and overseeing different users.
Doling out roles to new users can out you in a predicament:
giving them access to play out their errands with added permission to make
sweeping changes to your framework programming. If not, you could likewise play
safe by not giving them enough access to play out specific activities on the
framework. This is the place having the capacity to tweak and make new user roles
on your framework turns into a valuable capacity to have. Having fitting user roles
is urgent when allocating editors, creators and supporters of deliver and
oversee functionalities. The default user roles might be structured with
capacities that fit the prerequisites of present day framework, however fastidious
consideration must be taken while tweaking or updating the roles and consents
of users.
1. ONLY GIVE USERS THE LEVEL OF ACCESS
THEY NEED
This keeps your framework anchored, confining users from
making unapproved changes or keeping content safe from the danger of being
inadvertently erased. Before relegating a user, a role, evaluate what
undertakings they have to perform on the product and just allot them the role
that is fives them the capacities they need and nothing more.
2. RESTRICT HOW MANY USERS HAVE THE
ADMINISTRATOR ROLE
While some may suggest that an organization should keep just
a single head and relegate confided in individuals from the division the
manager role, this won't be handy in all cases. Sooner or later, other
colleagues may require more elevated amount get to. A few endeavors, may
require more elevated amount of access sooner or later of time. Extensive
organizations (like timeshare business) relegate administrator roles to a few
people. You have to ensure that the general population who have this role
utilize solid usernames and passwords with two-factor verification process. It
is prescribed to audit your administrators and reassign them new roles of
evacuate users where vital.
3. REGULARLY REVIEW USER ROLES AND
CAPABILITIES
CONCLUSION
Membroz membership software give a solid establishment to overseeing individuals and compose information in a deliberate request and streamline work functionalities. Such adaptable applications enable you to oversee and enable organizations to coordinate and deal with their most vital procedures.
membership software, membership management software, Club Management Software, Club Membership Software, Resort Management Software, Club Software, Gym Management Software, Gym Membership Software, Gym Software, Fitness Software, Yoga Studio Software, Timeshare Software, Vacation Ownership Management, Event Management Software, Online Event Planner, Event Planning Software, Event Software, Society Management Software, Housing Society Management Software, Housing Society Software, Apartment Management Software, Association Management Software, Association Membership Software, Association Software
membership software, membership management software, Club Management Software, Club Membership Software, Resort Management Software, Club Software, Gym Management Software, Gym Membership Software, Gym Software, Fitness Software, Yoga Studio Software, Timeshare Software, Vacation Ownership Management, Event Management Software, Online Event Planner, Event Planning Software, Event Software, Society Management Software, Housing Society Management Software, Housing Society Software, Apartment Management Software, Association Management Software, Association Membership Software, Association Software

Comments
Post a Comment